Connect ssh server use with .pem Key
Step (1) paste to .pem file (Ex. jeet.pem) for home
Step (2) open terminal type
:- $ su
:- $ password ********
:- # ssh -i jeet.pem username@domainname or server ip address
How to convert .PEM file to .PPK using PuTTYgen in Ubuntu
With *nix version of PuTTYgen:
# sudo puttygen <.pem filepath> -o <save filename.ppk>
Set permission
# chmod 777 -R <Save file name.ppk>
Then Follow this Step's
Step 1: Start Filezilla:- I hope you better know to how to start filezilla on your system. We can start filezilla using shortcut or through program files or command line.
Step 2: Add Key in Filezill:- Follow the given below screen-shots to add primary key in filezilla.


Some times filezilla prompt to convert key in case provided key is not in correct format which filezilla used. Feel free to convert file and save with some other name.
Step 3: Connect to SFTP Server
Enter the detail of Host, Username and Port ( if not using default ) and click on Quickconnect
1:- write_enable=YES
2:- chroot_local_user=YES
and you're getting following error when you log-in through ftp:
Error:- 500 OOPS: vsftpd: refusing to run with writable root inside chroot()
Solutions
you can fix the problem with adding following line to /etc/vsftpd.conf and restart the vsftpd service:
:- $ su
:- $ passwd
:- # sudo chown -R root:root /var/www/html/
:- # sudo nano /etc/vsftpd.conf
allow_writeable_chroot=YES (add this line or uncomment)
than restart vsftpd
:- # sudo service vsftpd restart
Command: PASS *****************
Response: 500 OOPS: could not read chroot() list file:/etc/vsftpd.chroot_list
Solution :-
:- $ su
:- $ password ********
:- # sudo nano /etc/vsftpd.conf (uncomment #chroot_list_enable=YES)
# Example config file /etc/vsftpd.conf
#
# The default compiled in settings are fairly paranoid. This sample file
# loosens things up a bit, to make the ftp daemon more usable.
# Please see vsftpd.conf.5 for all compiled in defaults.
#
# READ THIS: This example file is NOT an exhaustive list of vsftpd options.
# Please read the vsftpd.conf.5 manual page to get a full idea of vsftpd's
# capabilities.
#
#
# Run standalone? vsftpd can run either from an inetd or as a standalone
# daemon started from an initscript.
listen=YES
#
# Run standalone with IPv6?
# Like the listen parameter, except vsftpd will listen on an IPv6 socket
# instead of an IPv4 one. This parameter and the listen parameter are mutually
# exclusive.
#listen_ipv6=YES
#
# Allow anonymous FTP? (Disabled by default)
anonymous_enable=YES
#
# Uncomment this to allow local users to log in.
local_enable=YES
#
# Uncomment this to enable any form of FTP write command.
write_enable=YES
#
# Default umask for local users is 077. You may wish to change this to 022,
# if your users expect that (022 is used by most other ftpd's)
#local_umask=022
#
# Uncomment this to allow the anonymous FTP user to upload files. This only
# has an effect if the above global write enable is activated. Also, you will
# obviously need to create a directory writable by the FTP user.
#anon_upload_enable=YES
#
# Uncomment this if you want the anonymous FTP user to be able to create
# new directories.
#anon_mkdir_write_enable=YES
#
# Activate directory messages - messages given to remote users when they
# go into a certain directory.
dirmessage_enable=YES
#
# If enabled, vsftpd will display directory listings with the time
# in your local time zone. The default is to display GMT. The
# times returned by the MDTM FTP command are also affected by this
# option.
use_localtime=YES
#
# Activate logging of uploads/downloads.
xferlog_enable=YES
#
# Make sure PORT transfer connections originate from port 20 (ftp-data).
connect_from_port_20=YES
#
# If you want, you can arrange for uploaded anonymous files to be owned by
# a different user. Note! Using "root" for uploaded files is not
# recommended!
#chown_uploads=YES
#chown_username=whoever
#
# You may override where the log file goes if you like. The default is shown
# below.
#xferlog_file=/var/log/vsftpd.log
#
# If you want, you can have your log file in standard ftpd xferlog format.
# Note that the default log file location is /var/log/xferlog in this case.
#xferlog_std_format=YES
#
# You may change the default value for timing out an idle session.
#idle_session_timeout=600
#
# You may change the default value for timing out a data connection.
#data_connection_timeout=120
#
# It is recommended that you define on your system a unique user which the
# ftp server can use as a totally isolated and unprivileged user.
#nopriv_user=ftpsecure
#
# Enable this and the server will recognise asynchronous ABOR requests. Not
# recommended for security (the code is non-trivial). Not enabling it,
# however, may confuse older FTP clients.
#async_abor_enable=YES
#
# By default the server will pretend to allow ASCII mode but in fact ignore
# the request. Turn on the below options to have the server actually do ASCII
# mangling on files when in ASCII mode.
# Beware that on some FTP servers, ASCII support allows a denial of service
# attack (DoS) via the command "SIZE /big/file" in ASCII mode. vsftpd
# predicted this attack and has always been safe, reporting the size of the
# raw file.
# ASCII mangling is a horrible feature of the protocol.
#ascii_upload_enable=YES
#ascii_download_enable=YES
#
# You may fully customise the login banner string:
#ftpd_banner=Welcome to blah FTP service.
#
# You may specify a file of disallowed anonymous e-mail addresses. Apparently
# useful for combatting certain DoS attacks.
#deny_email_enable=YES
# (default follows)
#banned_email_file=/etc/vsftpd.banned_emails
#
# You may restrict local users to their home directories. See the FAQ for
# the possible risks in this before using chroot_local_user or
# chroot_list_enable below.
#chroot_local_user=YES
#
# You may specify an explicit list of local users to chroot() to their home
# directory. If chroot_local_user is YES, then this list becomes a list of
# users to NOT chroot().
# (Warning! chroot'ing can be very dangerous. If using chroot, make sure that
# the user does not have write access to the top level directory within the
# chroot)
chroot_local_user=YES
#chroot_list_enable=YES
local_root= /var/www/html/
# (default follows)
#chroot_list_file=/etc/vsftpd.chroot_list
#
# You may activate the "-R" option to the builtin ls. This is disabled by
# default to avoid remote users being able to cause excessive I/O on large
# sites. However, some broken FTP clients such as "ncftp" and "mirror" assume
# the presence of the "-R" option, so there is a strong case for enabling it.
#ls_recurse_enable=YES
#
# Customization
#
# Some of vsftpd's settings don't fit the filesystem layout by
# default.
#
# This option should be the name of a directory which is empty. Also, the
# directory should not be writable by the ftp user. This directory is used
# as a secure chroot() jail at times vsftpd does not require filesystem
# access.
secure_chroot_dir=/var/run/vsftpd/empty
#
# This string is the name of the PAM service vsftpd will use.
pam_service_name=vsftpd
#
# This option specifies the location of the RSA certificate to use for SSL
# encrypted connections.
rsa_cert_file=/etc/ssl/certs/ssl-cert-snakeoil.pem
# This option specifies the location of the RSA key to use for SSL
# encrypted connections.
rsa_private_key_file=/etc/ssl/private/ssl-cert-snakeoil.key
FTP Changes file permissions
:- $ su
:- $ password *********
:- # sudo nano /etc/vsftpd.conf
add this line
tcp_wrappers
Add this line
vsftpd: ALL
If you have any trouble on the installation procedures contact me on www.facebook.com/solveubuntu server support
Step (1) paste to .pem file (Ex. jeet.pem) for home
Step (2) open terminal type
:- $ su
:- $ password ********
:- # ssh -i jeet.pem username@domainname or server ip address
How to convert .PEM file to .PPK using PuTTYgen in Ubuntu
With *nix version of PuTTYgen:
# sudo puttygen <.pem filepath> -o <save filename.ppk>
Set permission
# chmod 777 -R <Save file name.ppk>
Then Follow this Step's
Step 1: Start Filezilla:- I hope you better know to how to start filezilla on your system. We can start filezilla using shortcut or through program files or command line.
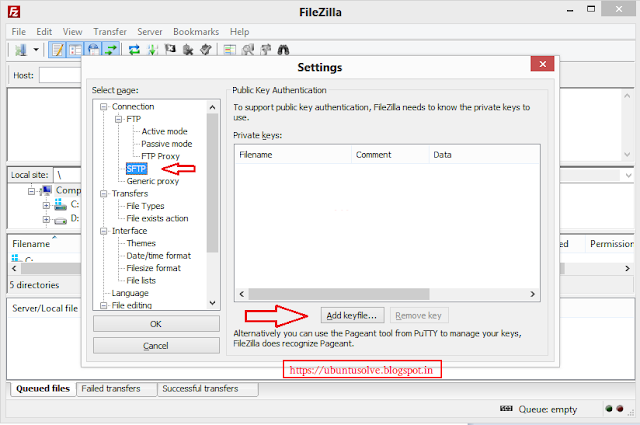
Step 2: Add Key in Filezill:- Follow the given below screen-shots to add primary key in filezilla.

2.2 Select SFTP under Connection and click Add key file.
2.3 Select private key file. You Key file will be added in List. Now Just click OK.

Some times filezilla prompt to convert key in case provided key is not in correct format which filezilla used. Feel free to convert file and save with some other name.
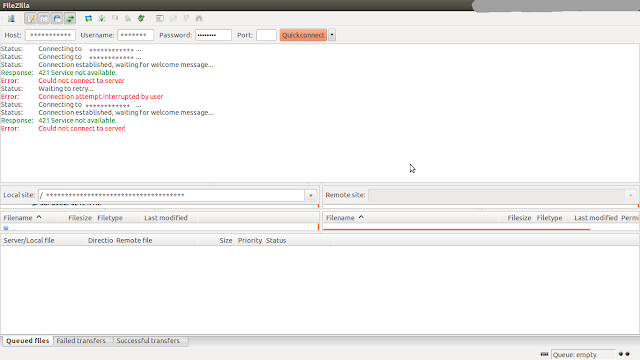
Step 3: Connect to SFTP Server
Enter the detail of Host, Username and Port ( if not using default ) and click on Quickconnect
500 OOPS: vsftpd: refusing to run with writable root inside chroot() errorIf you're using vsftpd with chroot local user option and write enable like this:

1:- write_enable=YES
2:- chroot_local_user=YES
and you're getting following error when you log-in through ftp:
Error:- 500 OOPS: vsftpd: refusing to run with writable root inside chroot()
Solutions
you can fix the problem with adding following line to /etc/vsftpd.conf and restart the vsftpd service:
:- $ su
:- $ passwd
:- # sudo chown -R root:root /var/www/html/
:- # sudo nano /etc/vsftpd.conf
allow_writeable_chroot=YES (add this line or uncomment)
than restart vsftpd
:- # sudo service vsftpd restart
Response: 331 Please specify the password.Command: PASS *****************
Response: 500 OOPS: could not read chroot() list file:/etc/vsftpd.chroot_list
Solution :-
:- $ su
:- $ password ********
:- # sudo nano /etc/vsftpd.conf (uncomment #chroot_list_enable=YES)
# Example config file /etc/vsftpd.conf
#
# The default compiled in settings are fairly paranoid. This sample file
# loosens things up a bit, to make the ftp daemon more usable.
# Please see vsftpd.conf.5 for all compiled in defaults.
#
# READ THIS: This example file is NOT an exhaustive list of vsftpd options.
# Please read the vsftpd.conf.5 manual page to get a full idea of vsftpd's
# capabilities.
#
#
# Run standalone? vsftpd can run either from an inetd or as a standalone
# daemon started from an initscript.
listen=YES
#
# Run standalone with IPv6?
# Like the listen parameter, except vsftpd will listen on an IPv6 socket
# instead of an IPv4 one. This parameter and the listen parameter are mutually
# exclusive.
#listen_ipv6=YES
#
# Allow anonymous FTP? (Disabled by default)
anonymous_enable=YES
#
# Uncomment this to allow local users to log in.
local_enable=YES
#
# Uncomment this to enable any form of FTP write command.
write_enable=YES
#
# Default umask for local users is 077. You may wish to change this to 022,
# if your users expect that (022 is used by most other ftpd's)
#local_umask=022
#
# Uncomment this to allow the anonymous FTP user to upload files. This only
# has an effect if the above global write enable is activated. Also, you will
# obviously need to create a directory writable by the FTP user.
#anon_upload_enable=YES
#
# Uncomment this if you want the anonymous FTP user to be able to create
# new directories.
#anon_mkdir_write_enable=YES
#
# Activate directory messages - messages given to remote users when they
# go into a certain directory.
dirmessage_enable=YES
#
# If enabled, vsftpd will display directory listings with the time
# in your local time zone. The default is to display GMT. The
# times returned by the MDTM FTP command are also affected by this
# option.
use_localtime=YES
#
# Activate logging of uploads/downloads.
xferlog_enable=YES
#
# Make sure PORT transfer connections originate from port 20 (ftp-data).
connect_from_port_20=YES
#
# If you want, you can arrange for uploaded anonymous files to be owned by
# a different user. Note! Using "root" for uploaded files is not
# recommended!
#chown_uploads=YES
#chown_username=whoever
#
# You may override where the log file goes if you like. The default is shown
# below.
#xferlog_file=/var/log/vsftpd.log
#
# If you want, you can have your log file in standard ftpd xferlog format.
# Note that the default log file location is /var/log/xferlog in this case.
#xferlog_std_format=YES
#
# You may change the default value for timing out an idle session.
#idle_session_timeout=600
#
# You may change the default value for timing out a data connection.
#data_connection_timeout=120
#
# It is recommended that you define on your system a unique user which the
# ftp server can use as a totally isolated and unprivileged user.
#nopriv_user=ftpsecure
#
# Enable this and the server will recognise asynchronous ABOR requests. Not
# recommended for security (the code is non-trivial). Not enabling it,
# however, may confuse older FTP clients.
#async_abor_enable=YES
#
# By default the server will pretend to allow ASCII mode but in fact ignore
# the request. Turn on the below options to have the server actually do ASCII
# mangling on files when in ASCII mode.
# Beware that on some FTP servers, ASCII support allows a denial of service
# attack (DoS) via the command "SIZE /big/file" in ASCII mode. vsftpd
# predicted this attack and has always been safe, reporting the size of the
# raw file.
# ASCII mangling is a horrible feature of the protocol.
#ascii_upload_enable=YES
#ascii_download_enable=YES
#
# You may fully customise the login banner string:
#ftpd_banner=Welcome to blah FTP service.
#
# You may specify a file of disallowed anonymous e-mail addresses. Apparently
# useful for combatting certain DoS attacks.
#deny_email_enable=YES
# (default follows)
#banned_email_file=/etc/vsftpd.banned_emails
#
# You may restrict local users to their home directories. See the FAQ for
# the possible risks in this before using chroot_local_user or
# chroot_list_enable below.
#chroot_local_user=YES
#
# You may specify an explicit list of local users to chroot() to their home
# directory. If chroot_local_user is YES, then this list becomes a list of
# users to NOT chroot().
# (Warning! chroot'ing can be very dangerous. If using chroot, make sure that
# the user does not have write access to the top level directory within the
# chroot)
chroot_local_user=YES
#chroot_list_enable=YES
local_root= /var/www/html/
# (default follows)
#chroot_list_file=/etc/vsftpd.chroot_list
#
# You may activate the "-R" option to the builtin ls. This is disabled by
# default to avoid remote users being able to cause excessive I/O on large
# sites. However, some broken FTP clients such as "ncftp" and "mirror" assume
# the presence of the "-R" option, so there is a strong case for enabling it.
#ls_recurse_enable=YES
#
# Customization
#
# Some of vsftpd's settings don't fit the filesystem layout by
# default.
#
# This option should be the name of a directory which is empty. Also, the
# directory should not be writable by the ftp user. This directory is used
# as a secure chroot() jail at times vsftpd does not require filesystem
# access.
secure_chroot_dir=/var/run/vsftpd/empty
#
# This string is the name of the PAM service vsftpd will use.
pam_service_name=vsftpd
#
# This option specifies the location of the RSA certificate to use for SSL
# encrypted connections.
rsa_cert_file=/etc/ssl/certs/ssl-cert-snakeoil.pem
# This option specifies the location of the RSA key to use for SSL
# encrypted connections.
rsa_private_key_file=/etc/ssl/private/ssl-cert-snakeoil.key

FTP Changes file permissions
vsftpd : limit connection to a set of IP addresses (Linux)
Seems you can use TCP Wrappers (just tested it on my Ubuntu) and use hosts.allow & hosts.deny to filter vsftpd access.
Add the following to your. vsftpd.conf file
:- $ password *********
:- # sudo nano /etc/vsftpd.conf
add this line
tcp_wrappers
Restart vsftpd.
:- # sudo nano /etc/hosts.denyAdd this line
vsftpd: ALL
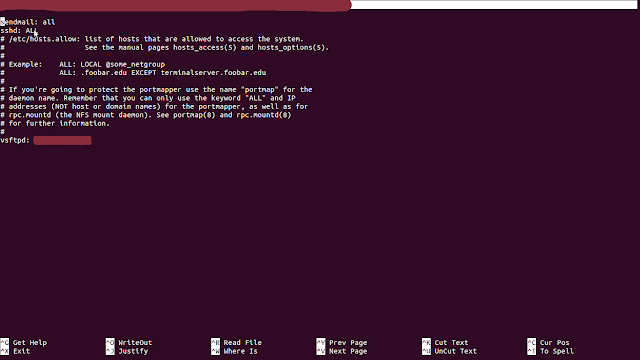
:- # sudo nano /etc/hosts.allow
sendmail: all
sendmail: all
sshd: ALL
# /etc/hosts.allow: list of hosts that are allowed to access the system.
# See the manual pages hosts_access(5) and hosts_options(5).
#
# Example: ALL: LOCAL @some_netgroup
# ALL: .foobar.edu EXCEPT terminalserver.foobar.edu
#
# If you're going to protect the portmapper use the name "portmap" for the
# daemon name. Remember that you can only use the keyword "ALL" and IP
# addresses (NOT host or domain names) for the portmapper, as well as for
# rpc.mountd (the NFS mount daemon). See portmap(8) and rpc.mountd(8)
# for further information.
#
vsftpd: IP Addess
(Example vsftpd: 192.168.1.1 192.168.20.10 125.120.5.1 192.168.10.2)
If you have any trouble on the installation procedures contact me on www.facebook.com/solveubuntu server support

No comments:
Post a Comment